Was this page helpful?
Caution
You're viewing documentation for a previous version. Switch to the latest stable version.
ScyllaDB Security Checklist¶
The Scylla Security checklist is a list of security recommendations that should be implemented to protect your Scylla cluster.
Enable Authentication¶
Authentication is a security step to verify the identity of a client. When enabled, Scylla requires all clients to authenticate themselves to determine their access to the cluster.
Role Base Access¶
Role-Based Access Control (RBAC), a method of reducing lists of authorized users to a few roles assigned to multiple users. RBAC is sometimes referred to as role-based security. It is recommended to:
Set roles per keyspace/table.
Use the principle of least privilege per keyspace/table. Start by granting no permissions to all roles, then grant read access only to roles who need it, write access to roles who need to write, etc. It’s better to have more roles, each with fewer permissions.
Encryption on Transit, Client to Node and Node to Node¶
Encryption on Transit protects your communication against a 3rd interception on the network connection. Configure Scylla to use TLS/SSL for all the connections. Use TLS/SSL to encrypt communication between Scylla nodes and client applications.
Starting with version 2023.1.1, you can run ScyllaDB Enterprise on FIPS-enabled Ubuntu, which uses FIPS 140-2 certified libraries (such as OpenSSL, GnuTLS, and more) and Linux kernel in FIPS mode.
Encryption at Rest¶
Encryption at Rest is available in a Scylla Enterprise 2019.1.1.
Encryption at Rest protects the privacy of your user’s data, reduces the risk of data breaches, and helps meet regulatory requirements. In particular, it provides an additional level of protection for your data persisted in storage or backup.
See:
Reduce the Network Exposure¶
Ensure that Scylla runs in a trusted network environment. A best practice is to maintain a list of ports used by Scylla and to monitor them to ensure that only trusted clients access those network interfaces and ports. The diagram below shows a single datacenter cluster deployment, with the list of ports used for each connection type. You should periodically check to make sure that only these ports are open and that they are open to relevant IPs only. Most of the ports’ settings are configurable in the scylla.yaml file. Also, see the list of ports used by Scylla.
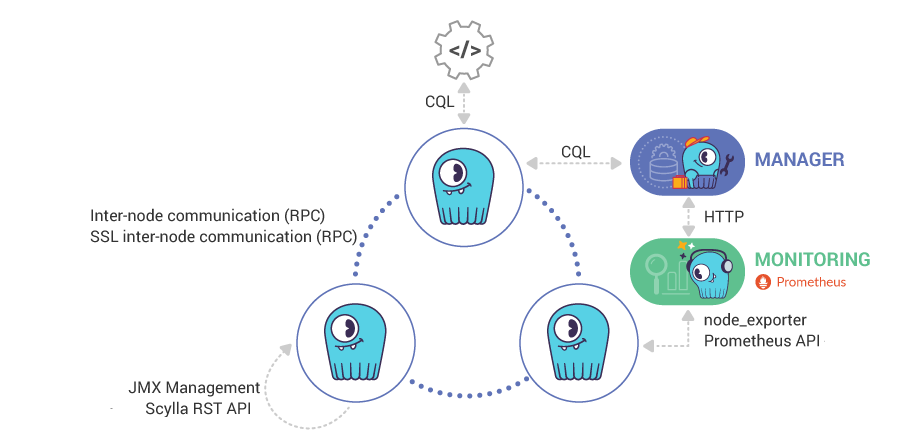
The Scylla ports are detailed in the table below. For Scylla Manager ports, see the Scylla Manager Documentation.
Scylla uses the following ports:
Port |
Description |
Protocol |
|---|---|---|
9042 |
CQL (native_transport_port) |
TCP |
9142 |
SSL CQL (secure client to node) |
TCP |
7000 |
Inter-node communication (RPC) |
TCP |
7001 |
SSL inter-node communication (RPC) |
TCP |
7199 |
JMX management |
TCP |
10000 |
Scylla REST API |
TCP |
9180 |
Prometheus API |
TCP |
9100 |
node_exporter (Optionally) |
TCP |
9160 |
Scylla client port (Thrift) |
TCP |
19042 |
Native shard-aware transport port |
TCP |
19142 |
Native shard-aware transport port (ssl) |
TCP |
Note
For Scylla Manager ports, see Scylla Manager <https://manager.docs.scylladb.com/>.
Audit System Activity¶
Using the auditing feature allows the administrator to know “who did / looked at / changed what and when.” It also allows logging some or all the activities a user performs on the Scylla cluster.
General Recommendations¶
Update your cluster with the latest Scylla version.
Make sure to update your Operating System, and libraries are up to date.
